API and Bot Attacks Costing Businesses Billions and Rising
Security
Zaker Adham
20 September 2024
26 August 2024
|
Paikan Begzad
Summary
Summary
Cado Security has uncovered a new threat to macOS users in the form of "Cthulhu Stealer," a malware-as-a-service (MaaS) program that disguises itself as well-known applications to infiltrate systems. This malicious software is designed to steal sensitive information from infected devices, including iCloud Keychain passwords, browser data, and Telegram account details.
According to Tara Gould, a researcher at Cado Security, Cthulhu Stealer deceives users by mimicking legitimate software like CleanMyMac, Grand Theft Auto IV, and Adobe GenP. When users attempt to run these counterfeit applications, macOS’s built-in security feature, Gatekeeper, alerts them that the software is unsigned. However, if users bypass this warning, the malware requests the system password under the guise of a legitimate prompt, enabling it to access critical data. Similar tactics are used by other macOS malware variants, such as Atomic Stealer, Cuckoo, MacStealer, and Banshee Stealer.
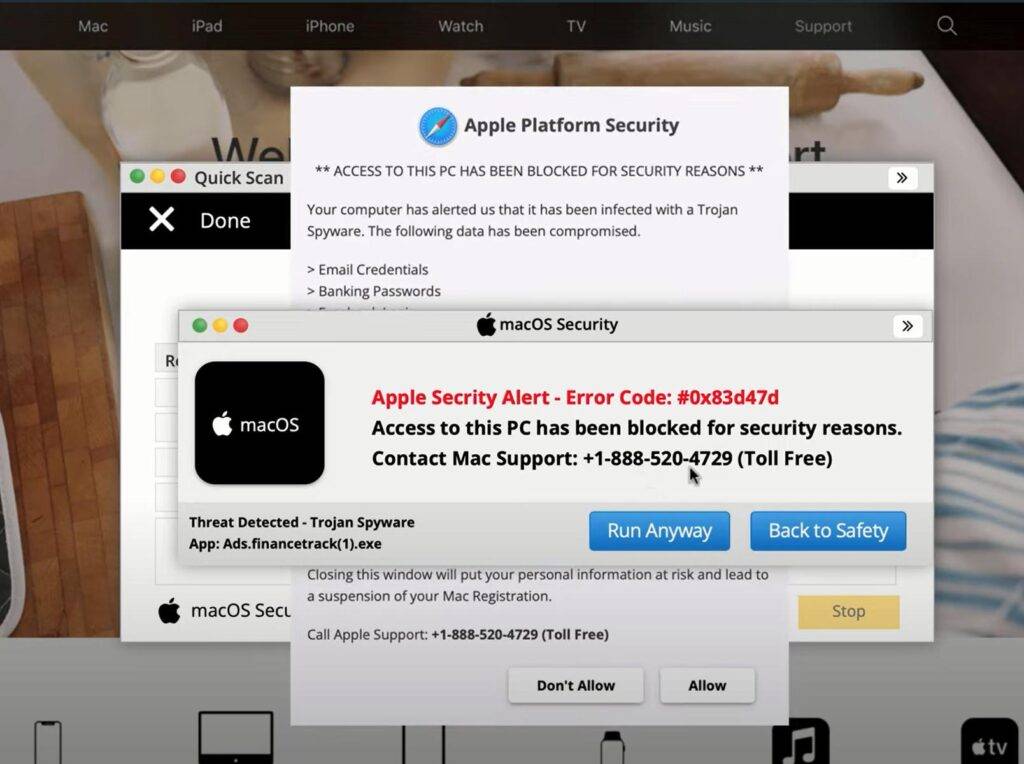
Cthulhu Stealer primarily focuses on extracting credentials and cryptocurrency wallets from various stores, including game accounts. Reports suggest that the malware's creators may have halted operations due to internal disputes, resulting in the main developer's ban from a cybercrime marketplace.
Despite the potential end of the Cthulhu Team, macOS users remain at risk. To protect against such threats, users should only download software from trusted sources like the Apple App Store, enable security features like Gatekeeper, keep their systems updated, and consider using reputable antivirus software.
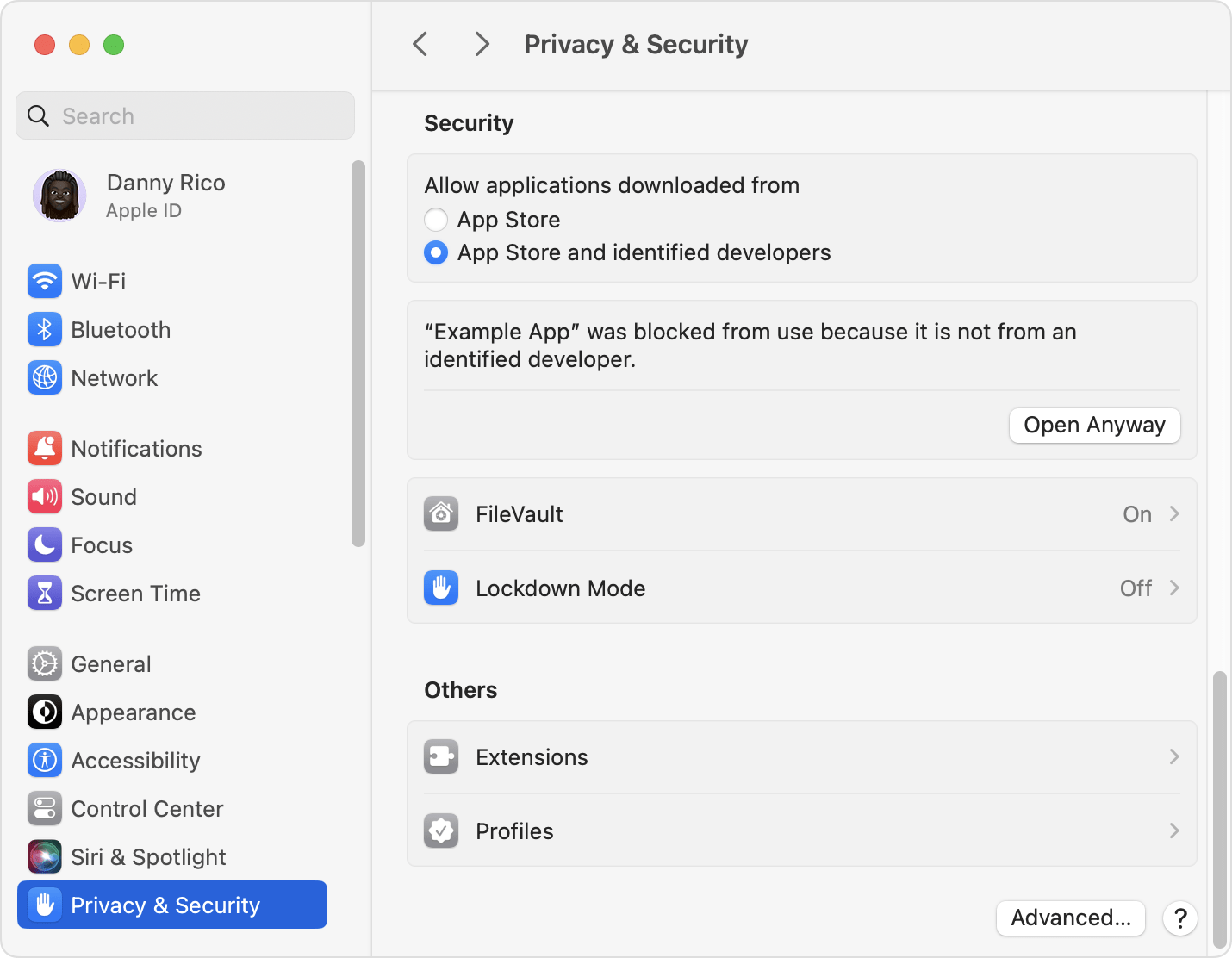
Apple's upcoming macOS Sequoia, expected in mid-September, aims to further tighten security by restricting the installation of unsigned software.

Security
Zaker Adham
20 September 2024

Security
Paikan Begzad
13 September 2024

Security
Zaker Adham
12 September 2024

Security
Zaker Adham
15 August 2024